Cyber Resilience Act

We support you in implementing the EU Cyber Resilience Act (CRA).
bytes at work translates the requirements of the EU CRA into efficient, repeatable, and auditable processes:
- SBOM generation
- Vulnerability management for Yocto Linux & Zephyr RTOS
- Secure update mechanisms
- Documentation
What is the CRA and when does it take effect?
The Cyber Resilience Act (Regulation EU 2024/2847) establishes mandatory security requirements for products with digital elements. It covers hardware, software, and firmware once a product is directly or indirectly connected to a network.
Manufacturers are required to demonstrably plan, implement, and document security measures throughout the entire product lifecycle. Depending on the assigned risk class, a conformity assessment by a notified body is required before the product can be placed on the market.

Note: The following text is for informational purposes only. The only legally binding and authoritative source is the official legislation published on the European Union’s website. Official CRA page: https://digital-strategy.ec.europa.eu/en/policies/cyber-resilience-act
Why act now
- Deadlines and CE requirements: The CRA is being implemented in stages. Starting early helps reduce transition costs and provides a buffer for conformity assessments.
- Liability and sanctions: Missing documentation increases audit and recall risks and can lead to significant fines or even sales bans.
Market expectations: OEMs now demand SBOMs, patch, and reporting processes. Without proof of compliance, approvals and tenders may be delayed.
- Quality throughout the lifecycle: Early automation improves the long-term security and reliability of releases and updates.
- Competitive advantage: Demonstrable security is becoming a key differentiator in procurement and partnership decisions.
Our CRA Services
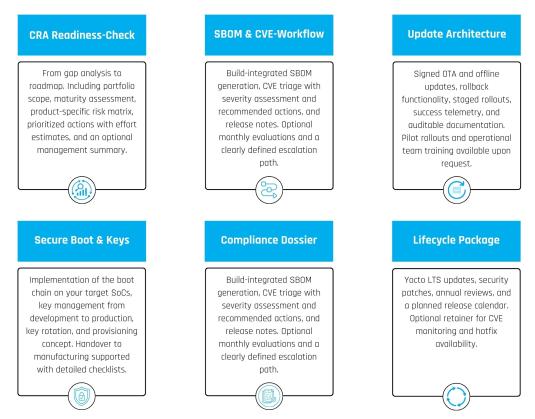
Everything is modular and tailored to your specific needs and requirements.
Your Benefits
- Achieve compliance systematically: A clear roadmap, defined responsibilities, auditable artifacts, and complete traceability.
- Audit-ready from the pipeline: Build-integrated SBOMs, automated CVE triage, and reproducible releases with full documentation.
- Security in the field: Secure boot, controlled key management, and signed updates with staging and rollback functionality.
- Less manual effort: Standardized templates, automation, and clear escalation paths reduce errors and turnaround times.
- Secure planning and market access: Modular packages with defined deliverables enable faster CE and OEM approvals.



